The Mitre Att&ck Matrix has defined nine techniques to cover initial access activities in a […]
Resource Development (Mitre Att&ck Matrix)
To define Resource Development, the Mitre Att&ck Matrix has defined seven techniques to cover the […]
Reconnaissance Techniques (Mirtre Att&ck Matrix)
The MITRE Att&ck Matrix has specified ten techniques to classify as reconnaissance. Active-Scanning means the […]
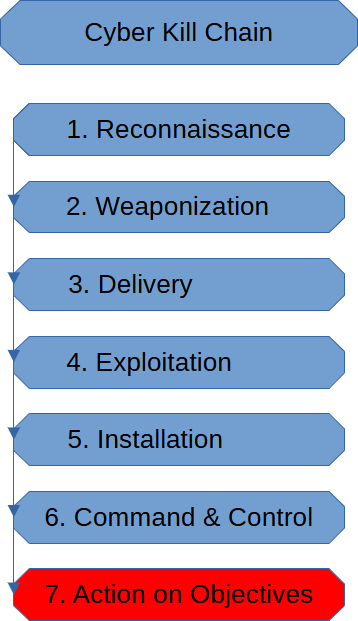
Actions On Objectives (Cyber Kill Chain)
The Actions On Objectives Stage is the end of a Cyber Attack. The threat actor […]
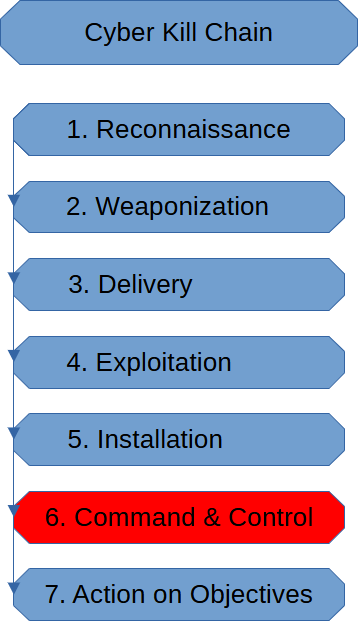
Command & Control Stage (Cyber Kill Chain)
The Command & Control Stage of the cyber kill chain is when the threat actor […]
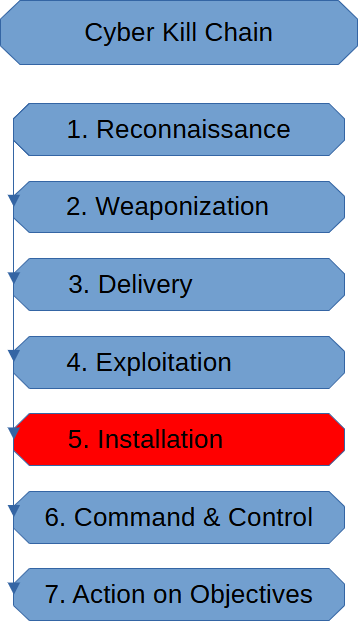
Installation Stage (Cyber Kill Chain)
The Installation Stage of the Cyber Kill Chain is when the threat actor establishes a […]
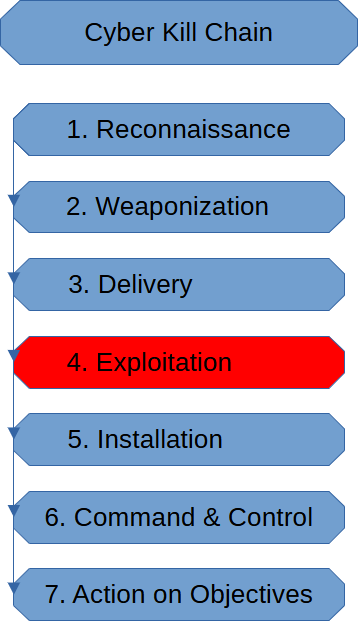
Exploitation Stage (Cyber Kill Chain)
The Exploitation Stage is when we successfully execute the exploit we planned during the reconnaissance […]
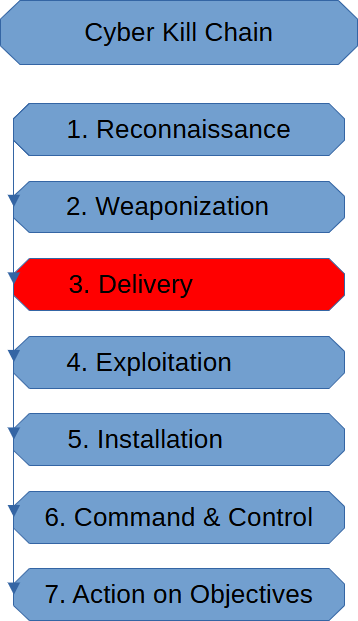
Delivery Stage (Cyber Kill Chain)
The Delivery Stage of the Cyber Kill chain is when the threat actor has decided […]
Weaponization Stage (Cyber Kill Chain)
Weaponization in the cyber kill chain uses the intel the threat actor obtained from the […]
Reconnaissance Stage (Cyber Kill Chain)
The Reconnaissance Stage of the Cyber Kill Chain is where the threat actor probes their […]