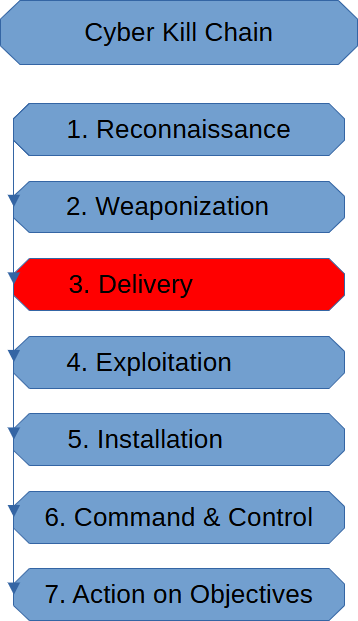
The Delivery Stage of the Cyber Kill chain is when the threat actor has decided […]
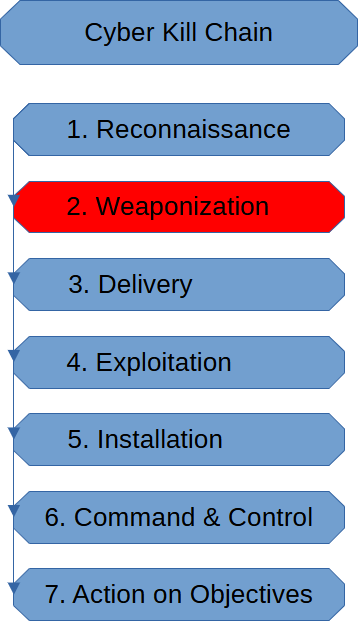
Weaponization Stage (Cyber Kill Chain)
Weaponization in the cyber kill chain uses the intel the threat actor obtained from the […]
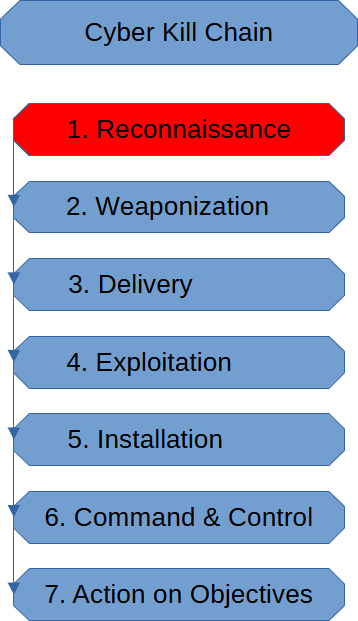
Reconnaissance Stage (Cyber Kill Chain)
The Reconnaissance Stage of the Cyber Kill Chain is where the threat actor probes their […]
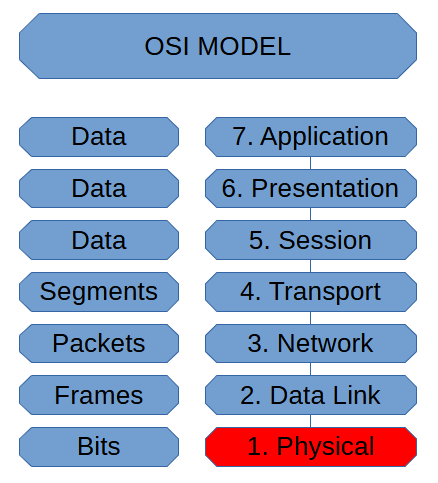
Physical Layer (OSI Model)
The Physical Layer is where we finally transmit our data. It is also when we […]
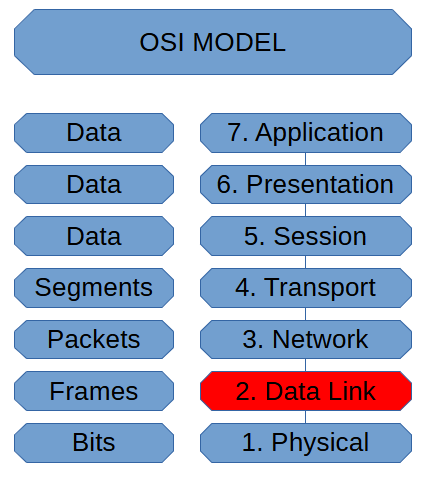
Data Link Layer (OSI Model)
The Data Link is where we handle Media Access Control operations. It’s also how we […]
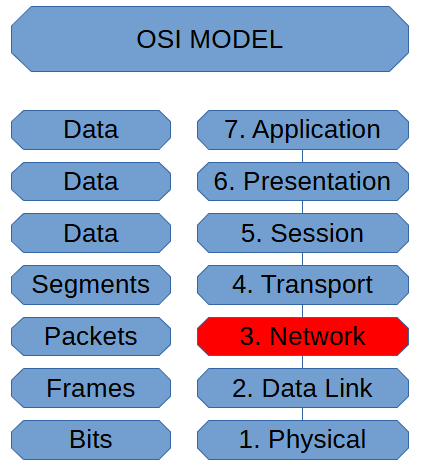
Network Layer (OSI Model)
The Network Layer of the OSI Model is where we have packets. These packets don’t […]
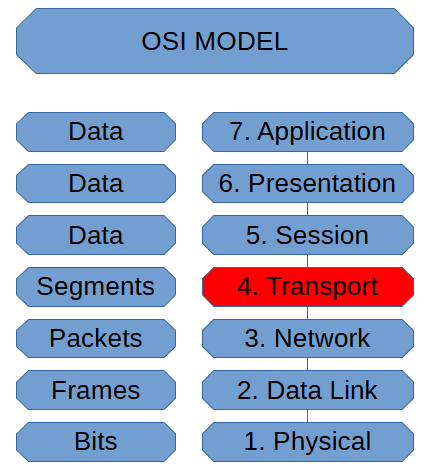
Transport Layer (OSI Model)
The Transport Layer of the OSI Model is where protocols such as UDP and TCP […]
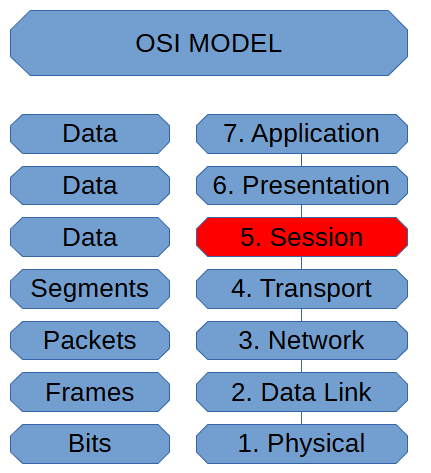
Session Layer (OSI Model)
The session layer of the OSI Model is where sessions get managed. Being able to […]
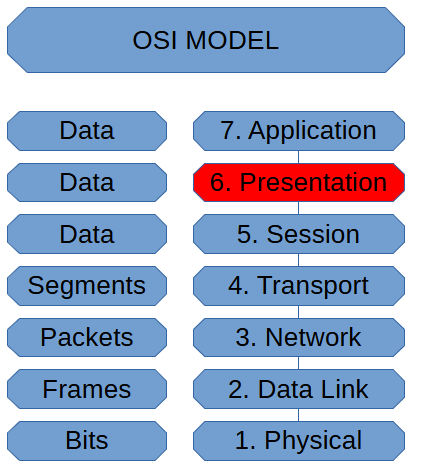
Presentation Layer (OSI Model)
In the OSI Model, the Presentation Layer is where we format, compress, or encrypt, ensuring […]
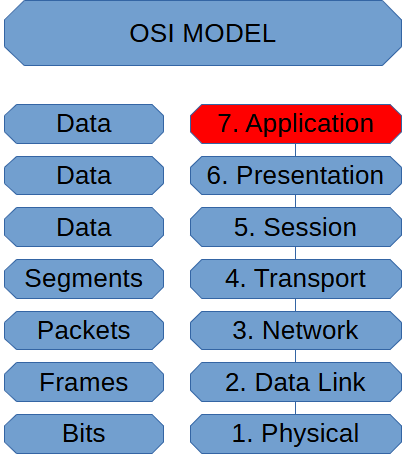
Application Layer (OSI Model)
The Application layer is where Network Traffic Begins and Ends. When we initiate network traffic, […]