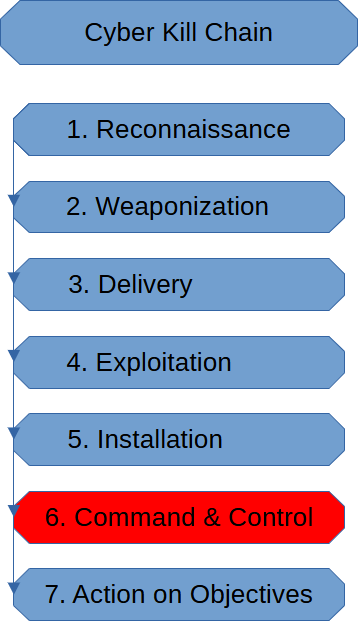
The Command & Control Stage of the cyber kill chain is when the threat actor establishes persistence.
Not every cyber attack deals with persistence the same. Ransomware might not be persistent as other cyber attacks are. The threat actor likely has some control, such as issuing commands to decrypt the data.
Though generally, with persistence, we deal with a Command & Control (c2) system. A c2 system gives a threat actor direct access to a system as well as utilities that can exfiltrate data, obtain credential hashes, or even generate a Golden Ticket to be able to pivot across the network.