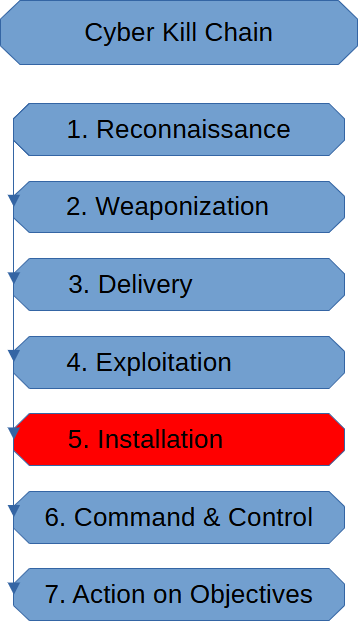
The Installation Stage of the Cyber Kill Chain is when the threat actor establishes a foothold in the target’s infrastructure. The victim of the attack should start to notice signs of an attack if they are monitoring.
In a ransomware attack, this is where the ransomware malware initializes and starts encrypting.
In attacks where the threat actor desires persistence, the threat actor installs the malware for persistence.