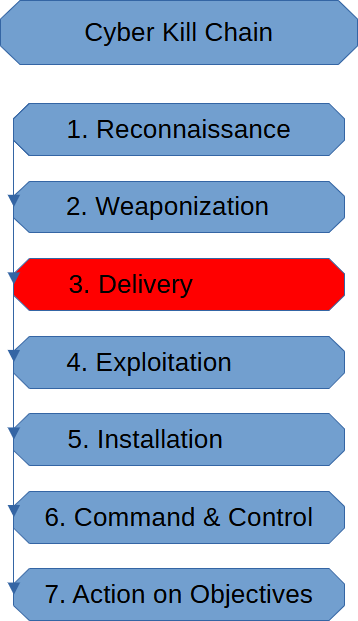
The Delivery Stage of the Cyber Kill chain is when the threat actor has decided on a method to deliver the malware the threat actor created.
One popular method of delivering malware is a variant of phishing. It may not be a phishing attack in the sense of going after credential harvesting, but the same methodology to trick a victim into executing your payload applies. This technique is particularly effective when you are after a specific target.
Another less reliable method can be loading the malware on a USB Flash Drive rigged to automatically launch the payload and leave it somewhere so that a victim that works for your target organization finds it and plugs it in an attempt to identify who it belongs to, unknowingly letting malware in.
Another method that can work alongside emails is having a server mimicking a target server in a man-in-the-middle attack designed to redirect users to the malicious payload that appears to be a regularly used application over the network. This technique can work alongside an email, as described in the first example.
No matter the tactics used, the Delivery Stage is when we deliver the exploit to our target’s infrastructure.