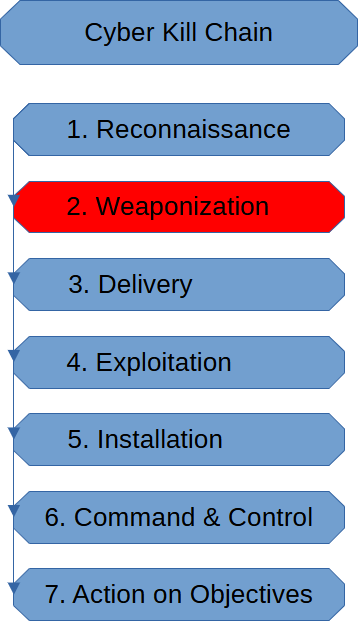
Weaponization in the cyber kill chain uses the intel the threat actor obtained from the reconnaissance stage to create a suitable piece of malware to infect their target.
The specific malware used will depend on the objectives of the threat actor and what the threat actor’s intel suggests should work. It is pointless to set up windows based malware if the target organization runs macs!
Let’s say that the threat actor discovers the target organization is running an insecure email client that automatically opens .pdfs upon reception. Then we develop a malware solution that gets embedded into a pdf.