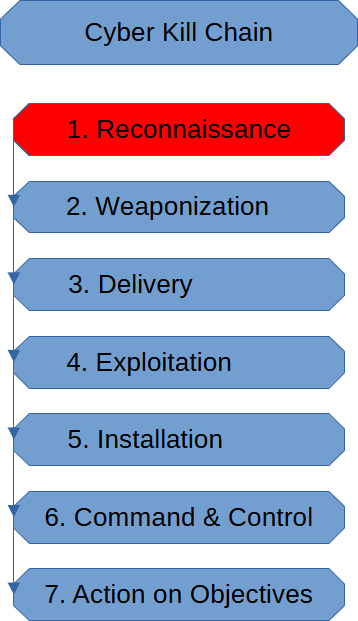
The Reconnaissance Stage of the Cyber Kill Chain is where the threat actor probes their target as thoroughly as he/she can so that the threat actor can gather as much intel as he/she can.
The Recon Stage is also where things such as port scanning and vulnerability discovery take place. Credential harvesting is another recon activity.
Most information found that can be useful in carrying out a cyber-attack is typically found in the recon stage.
The threat actor proceeds forward in the Cyber Kill Chain once enough intel is collected.